On the provider’s website, you may obtain a Critical Information Summary for all their plans. Communications providers give customers with this paper, which outlines the costs and benefits associated with their services. You may readily compare one service provider’s pricing and service to another since the information is given in the same style.
5 Keyword Research Tips For SEO & PPC
It does not matter what you are doing, research is the key to everything.
When you are operating a business, it is normal that you will work to improve your online presence. You will always want to rank among the top pages of the SERP or search engine result page.
How coders help online casinos and bingo sites
The gambling industry boom during the 21st century has undoubtedly proved to be a Godsend for software developers across the world.
From online casinos to bingo sites in UK, need the iGaming sector since it is heavily reliant on people who have the ability to develop software.
In simple terms, coders contribute to the development of online gambling games and work on other elements such as integrating payment gateways.
Let’s take a closer look at how coders help online casinos and bingo sites.
How gambling and bingo sites are developed
Designing an online gambling site is a labour-intensive affair which generally involves input from approximately 10-12 people.
The team includes software developers, who handle elements such as coding the software and determining which programming language to use.
These include C++, HTML5, C#, Java, JavaScript, PHP, Python and SQL, all of which are suitable to be used to power an online gambling site.
Software developers also handle design user interfaces, the application programming interface (API) and security and compliance controls.
At each stage in the process, the developer will test the software to ensure it takes clean inputs, processes data accurately and generates perfect outputs.
The process starts with the developer collecting information from the client on what they are looking to achieve with the online bingo website.
The developer takes this information and translates it to software requirements, which is then used to write the code for the site.
Once the code is written, this is incorporated with other elements from the design process to produce a finished version of the bingo site.
Integrating the site’s mechanics
Online gambling sites are made up of several key components, each of which must be successfully integrated to create a positive experience for the user.
Payment methods play a key role, providing players with an easy way to make deposits and request withdrawals if they are lucky enough to win.
The skills of software developers are crucial in this regard, as they design APIs that support integration with financial service providers.
With payment options evolving at a rapid rate, it is imperative for coders to keep up to speed with the latest developments in this area.
Another hugely important part of the coding process involves the random number generator (RNGs), which is the mechanism which delivers the results for each game.
Every country has rules governing RNGs, which are issued by the appropriate iGaming authority within a particular jurisdiction.
If the client offers their services in several different regions, the developer must ensure that multiple versions of the RNG are created to comply with local legislation.
With online gambling or bingo operators subject to frequent testing by independent auditors over the fairness of their sites, it is imperative that the RNG lives up to expectations.
Launching and maintaining the gambling site

When the software has been fully tested and the client is satisfied it meets their needs, the online gambling site can go live on the internet and players can start enjoying bingo games.
Software developers continue to provide support when the site is launched to ensure that everything continues to work as it should.
This includes updating the software as needed, the provision of additional functionality, removing unwanted functions or implementing site enhancements.
However, the main responsibility for a developer once a site is live is ensuring that any software bugs are swiftly identified and eradicated.
While all gambling sites must undergo stringent testing before they are launched, it is virtually impossible to ensure that every bug is fixed.
With players often wagering large sums of money, it is imperative that gambling sites run smoothly and remain stable across all devices.
If a site crashes due to bugs, there is the potential for players to lose a significant portion of their bankroll through no fault of their own.
It is also essential for the developer to ensure that any security vulnerabilities are pinpointed early, to prevent hackers from causing unwanted harm to the site.
Optimising the site for mobile
As we have already mentioned, online gambling sites must be designed to work seamlessly across all digital devices.
For the software developer, this means that the site must be coded to load without a hitch on desktop, laptop, tablet and mobile.
In an age where people spend an average of more than four hours per day on their smartphones, online gambling operators cannot afford to neglect their mobile offering.
As a bare minimum, the site should be easy to access on smaller devices and offer all the same features that are available on desktop and tablet.
However, some gambling operators go the extra mile by investing resources into developing standalone casino and bingo apps.
The process to create an app bears many similarities to developing a website, and requires the same level of attention to detail from a coding perspective.
A quick look at some of the negative reviews on the Google Play Store and App Store highlights that many gambling operators fail to appreciate the importance of app development.
The operators who get this element right are the ones who fully recognise the worth of utilising talented software developers to develop gambling apps.
Best tips to play online
Are you an online casino beginner? If your answer is yes, then you are probably looking out for some tips to play casino games like a pro. You are at the right place. Here in this page, you will find a list of simple and easy ways to play casinos like a pro. With the help of these tips and tricks, you will be able to enjoy playing games at your favorite casino. Furthermore, you will learn more about what to look in a specific online casino. Get ahead of the pack with the best casino gambling experience you can get.Continue reading →
Makita 18v planer – a tool for efficient woodwork
For efficient woodwork during renovation or construction, specialists and amateurs use special appliances — planers (for example, high-tech Makita 18V planer). This power tool can easily process the hardest boards. It gives the material a smooth and pleasant surface, so even the rough wood can look like a work of art. Therefore, Makita 18V cordless planer is so popular. Such power tools are suitable for both professional and home use.Continue reading →
Importance to upgrade to Skrill VIP through ewalletvip
Registered members to Skrill using E-wallet VIP have reduced requirements for the VIP levels. Therefore, it is easier for these members to quickly move from one level to another compared to a normal member. In relation to your daily transaction habits, it is likely to save you a lot in reduced fees and benefits. In addition, E-wallet awards its clients with a free Skrill upgrade on the first two levels. Due to this reason, it is more of an advantage for clients to upgrade to skrill VIP through ewalletvip because of their huge offers and the benefits given out.Continue reading →
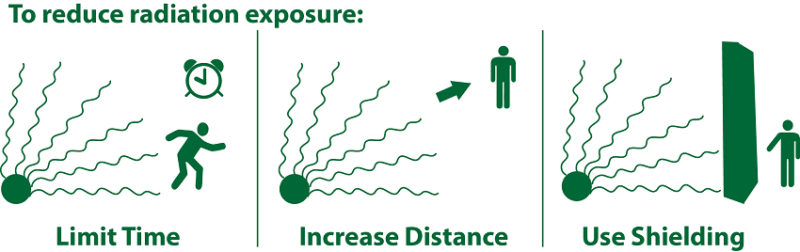
3 Core Ways for Radiation Exposure Control
The effects of radiation can send a chill down anyone’s spine, especially after what happened at Chernobyl and Japan’s Fukushima. These effects were not only felt by the workers at the plants, but also by the communities around the plants. Some people bought iodine pills after the meltdown at Fukushima out of fear that radiation could cross the Pacific Ocean.Continue reading →
How to recognize abusive relationships: five signs
What is abuse and, namely, abusive relationships? Today we hear it on every street corner. TV, Internet, streaming platforms – they all warn us from this kind of romance that, in fact, has absolutely nothing to do with love.Continue reading →
How does electronic design automation work?
Electronic design automation (EDA) provides a solution to the growing complexity of integrated circuit development by providing hardware and software that enables engineers to design, verify, and manufacture complex systems-on-chips. First, let’s discover how electronic design automation work.Continue reading →
How to get started in eSports and what career to choose
One of the biggest eSports competitions in the world, International 10, finished not long ago. 18 teams contested for the grand prize of $18.2 million at the videogame Dota 2. The prize pool mainly consists of the money that the fans of the game spent on it. It grew so much because there was no event last year because of Covid. The underdogs of the tournament, Team Spirit (Russia), won the contest. Only the brave bettors, who chose the gambling operator here at the Bookmaker Ratings, made a bet on them with odds at 70/30 in favor of their opponent PSG.LGD, won.Continue reading →